
Access PostgreSQL Database via Cloudflare Zero Trust / Cloudflare Access / Cloudflare Tunnel
Using Cloudflare Zero Trust/Access/Tunnel, we can access self-hosted internal resources securely, through Cloudflare’s network, without exposing the internal resources to the public internet.
While securing internal web apps has been a smooth sailing experience for me (following the Cloudflare Zero Trust guide), I have not found any guide on how to secure access to a PostgreSQL database through Cloudflare Zero Trust/Access/Tunnel.
At the end of this post, you will be able to access your PostgreSQL database using Cloudflare WARP, via Cloudflare Zero Trust/Access/Tunnel.
Links to official documentation:
PostgreSQL database Cloudflare Zero Trust Cloudflare Access Cloudflare Tunnel Cloudflare WARPPrerequisites
- Server is connected to Cloudflare’s network (via Cloudflare Tunnel)
Get the IP address of the PostgreSQL database
We need the IP address of the PostgreSQL database to be able to access it via Cloudflare WARP. Connecting using hostname is not supported.
If you are using Docker, you can get the IP address of the PostgreSQL database by running the following command:
docker inspect -f '{{range.NetworkSettings.Networks}}{{.IPAddress}}{{end}}' [id of container]
However, the IP address of the container is not stable, and it might change when the container is restarted. Follow this guide to set a static IP address for the container.
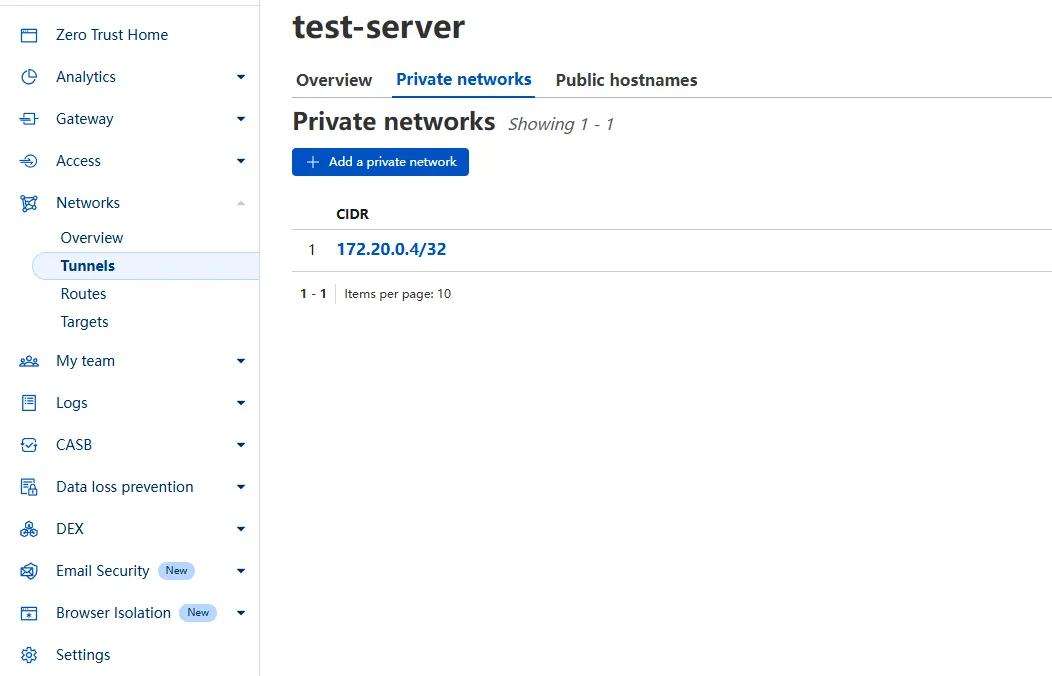
Create a private network
Ref: Cloudflare Zero Trust Private Network
Go to Networks > Tunnels, select and configure your tunnel.
Go to Private networks > Add a private network.
Enter the IP address of the PostgreSQL database, and click “Save”.
Download WARP client
Download WARP client on your device.
Go to Preferences and sign in to your Zero Trust team.
Make sure you have allowed devices to join with WARP client.
Configure WARP profile
If the IP address of the PostgreSQL database is an internal IP address, you need to configure a WARP profile to route traffic through the WARP client.
Go to Settings > WARP Client > Device settings > Profile settings, create or select a profile.
Edit the profile and go to Split Tunnels > Manage.
If the mode is set to Exclude, make sure the IP address of the PostgreSQL database is removed from the list.
Connect to the PostgreSQL database
You can now access the PostgreSQL database via the IP address when WARP client is enabled and connected.